As microservices continue to gain popularity, it is important to consider the security implications of this architecture. A microservice architecture can bring many benefits in terms of scalability, maintainability, and flexibility, but it also introduces new security challenges. This blog post will explore the most important aspects of securing a microservice architecture, including the following things.
- Authentication and Authorization: How to ensure that only authorized users and services can access the microservices.
- Data Protection: How to protect sensitive data that is transmitted between microservices.
- Network Security: How to secure the network infrastructure that connects the microservices.
- Service Isolation: How to ensure that each microservice is isolated and protected from other services.
- Monitoring and Logging: How to monitor the system for security breaches and ensure that logs are being properly collected and analyzed.
By addressing these security concerns, we can ensure that our microservice architecture is secure and can be trusted to handle sensitive data and critical operations. If you haven’t read the previous parts of this miniseries I highly recommend you do that:
Part 1 – How to build a microservice
Part 2 – Microservice communication
Part 3 – Monitoring and Observability
Monitoring and Logging
Let’s quickly review what we went through in part 3; As we discussed, monitoring and logging are essential aspects of securing a microservice architecture. Proper monitoring and logging can help detect and respond to security breaches and other issues that may arise within the system.
To ensure proper monitoring, it is important to collect and analyze logs from all the microservices and their underlying infrastructure. This includes logs from the operating system, web servers, databases, and other components of the system.
In addition to logging, it is also important to set up metrics and alerts to monitor the health and performance of the microservices. This can help identify issues before they become security risks and ensure that the system is running smoothly.
Overall, monitoring and logging are critical components of securing a microservice architecture. By properly monitoring and logging the system, we can quickly detect and respond to security threats and ensure that the system is running smoothly. Read more about this in part 3.
Authentication and Authorization
Authentication is another crucial aspect of securing a microservice architecture. It ensures that only authorized users or services can access the microservices and their resources.
gRPC, a high-performance, open-source remote procedure call (RPC) framework, provides a built-in authentication layer that allows for secure communication between microservices. The gRPC authentication layer supports several authentication mechanisms, including Transport Layer Security (TLS) and Token-based authentication.
On the other hand, REST or other types of services may use other means of authentication, such as OAuth, JSON Web Tokens (JWT), or Basic Authentication. These authentication mechanisms require additional configuration and setup, but they can provide a secure and flexible way to authenticate users and services.
Regardless of the authentication mechanism used, it is important to implement proper authentication and authorization controls in each microservice. This includes ensuring that only authorized users and services can access the microservices and their resources, and that access controls are enforced at the API level.
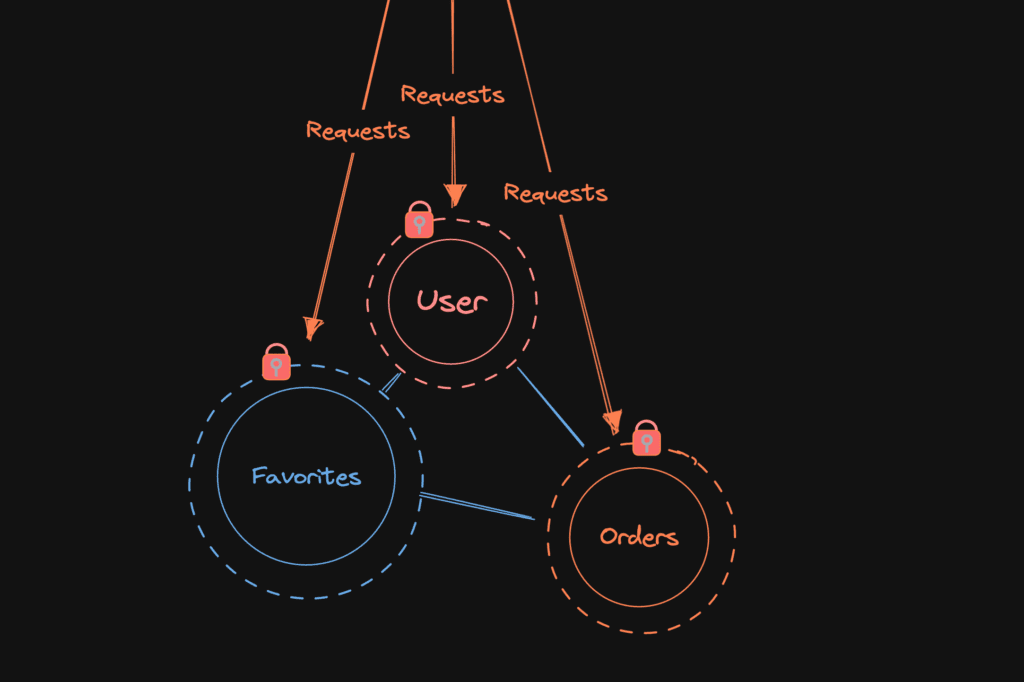
Moreover, it is important to choose an authentication mechanism that aligns with the needs of the microservice architecture and the security requirements of the system. By selecting the appropriate authentication mechanism and implementing proper authentication and authorization controls, we can ensure that our microservice architecture is secure and only accessible to authorized users and services.
Service Isolation
As the name suggests, service isolation refers to the practice of keeping individual services separated from one another, both logically and physically.
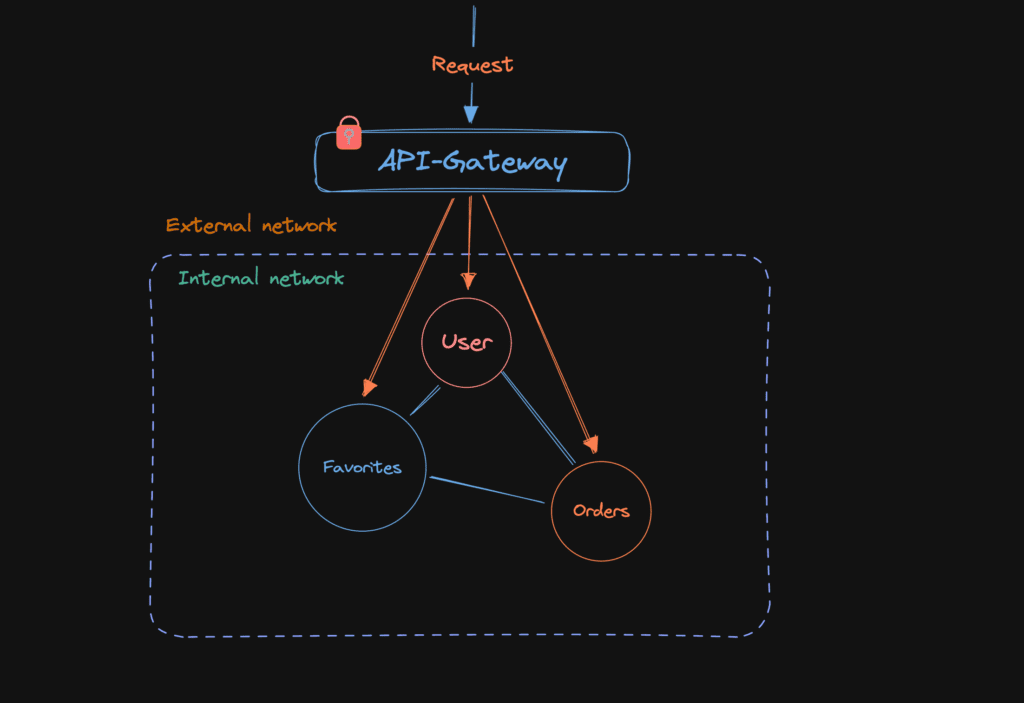
Logical Isolation focuses on minimizing the interdependence between microservices. Each service should be designed to have its own functionality and boundaries. One of the key benefits of logical isolation is to prevent unauthorized access. The principle of least privilege comes into play here, as each microservice should only have access to the data and resources it requires to perform its designated tasks. To achieve logical isolation, it is crucial to establish well-defined and granular APIs between microservices.
Physical Isolation focuses on the underlying infrastructure, separating resources or containers. By running its own isolated environment, vulnerabilities or breaches in one microservice are less likely to impact the security of other services. Docker is a popular choice to achieve physical isolation, as each microservice runs in its own container, which provides an additional layer of security.
When implementing service isolation, it is essential to have a good balance between security and operation efficiency. Too strict security and the might performance suffer, it will also increase complexity and increase the resource usage of each service.
Network security
Network security is a critical aspect of ensuring the protection and integrity of microservices. It involves implementing measures to secure the network infrastructure and communications between microservices. Key components of network security include firewall configuration, network segmentation, and intrusion detection and prevention systems. Firewalls act as a barrier, controlling and monitoring incoming and outgoing traffic. Network segmentation helps isolate microservices, limiting the potential impact of a security breach. Intrusion detection and prevention systems actively monitor network traffic for suspicious activities, detecting and mitigating potential threats. By implementing robust network security measures, organizations can enhance the overall security posture of their microservices architecture and protect against unauthorized access and data breaches.
Data protection
Data protection is of utmost importance when it comes to microservices. It involves implementing measures to safeguard the confidentiality, integrity, and availability of data within the microservices architecture. Encryption is a fundamental technique used to protect sensitive data both in transit and at rest. Access controls, such as authentication and authorization mechanisms, should be implemented to ensure that only authorized users or services can access and manipulate data. Regular backups and disaster recovery plans help protect against data loss and ensure business continuity. Additionally, monitoring and auditing mechanisms should be in place to detect and respond to any potential data breaches or unauthorized access attempts. By prioritizing data protection in microservices, organizations can maintain the privacy and security of their valuable data assets.
A few tips on securing your microservices
Here are a few tips and best practices when securing a microservice architecture:
- Role-based Access Control (RBAC): RBAC allows access control decisions based on roles and permissions, ensuring only authorized users or services can access microservices and resources. Pros: Flexible, scalable, and integrates with existing IAM systems. Cons: Complexity in implementation and maintenance for large architectures.
- TLS/SSL for secure communication: TLS/SSL encrypts and authenticates communication between microservices, securing data from unauthorized access. Pros: Provides secure data transmission and easy integration. Cons: Can impact performance and complex setup, especially in complex architectures.
- API Gateway: An API Gateway acts as an entry point, handling authentication, authorization, and other security tasks. Pros: Centralized security management, simplifies development and maintenance. Cons: Single point of failure and potential latency in communication.
- Containerization and Orchestration: Docker and Kubernetes offer security benefits like isolation and easy deployment, scaling, and management. Pros: Additional security, simplifies deployment and management. Cons: Complexity and maintenance challenges, especially in large systems.
By implementing these tips and best practices, we can ensure that our microservice architecture is secure and can be trusted to handle sensitive data and critical operations.
Final words
As I am no security expert this part contains mostly general guidelines on securing software. Each technology requires too much configuration for us to cover in a single blog post. But here are some tips you can follow in your daily work:
- Implement services with a “need to know” basis. Don’t share data for the sake of sharing it.
- Secure your endpoints and limit the access to bare minimum, it’s easier to grant access than revoke access.
- Regularly update and patch software dependencies and libraries to address known vulnerabilities. Keeping your software up to date helps protect against known security risks and exploits.
- Follow secure coding practices, such as input validation, output encoding, and proper error handling, to prevent common security vulnerabilities like cross-site scripting (XSS) and SQL injection attacks.
- As a last one, Test your code!
The final part will be about testing. Until then!
Part 1: The Pros and Cons of Microservices: Is It Right for Your Project?
Part 2: Building a Robust Microservice Architecture: Understanding Communication Patterns
Part 3: The Importance of Monitoring and Observability in Microservice Architecture
Part 4: Securing a Microservice Architecture – 5 Pillars
Part 5: Testing in Microservices: Ensuring Quality and Reliability